The core purpose of TIC is to provide a strategic perspective on the threats, enabling proactive defense measures and informed decision-making.
What is Threat Intelligence Capability?
TIC involves the application of tools and processes to gather and scrutinize data that could indicate a threat to the organization’s digital environment.
It goes beyond mere data collection to analyze the intentions, capabilities, and opportunities of potential attackers. This includes tracking adversary tactics, techniques, and procedures (TTPs), and applying this knowledge to predict and prevent future attacks.
Effective TIC is characterized by its ability to translate technical threat indicators into contextual intelligence that informs security strategies and policies.
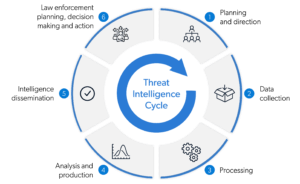
The Importance of TIC in the Education Sector
For the education sector, building an effective TIC is not a luxury but a critical defense mechanism. Educational institutions are rich targets due to the sensitive data they hold, such as personal information of students and faculty, financial records, and proprietary research data.
As such, a TIC provides a strategic framework to identify and mitigate cyber threats, safeguarding the reputation and the very mission of these institutions.
Components of Threat Intelligence Capability
To build an effective TIC, certain foundational components must be established:
1. Data Collection and Analysis
- Sources of Data: Collect data from various sources such as internal network logs, threat intelligence feeds, and incident reports.
- Analysis Tools: Use advanced analytical tools like SIEM systems to process and analyze the collected data.
2. Threat Intelligence Feeds
- Integration: Incorporate feeds into cybersecurity systems to provide real-time data on potential threats.
- Customization: Customize feeds to the specific threats relevant to the education sector.
3. Incident Response and Management
- Incident Response Plan (IRP): Develop an IRP tailored to the types of threats the education sector faces.
- Training and Simulations: Conduct regular training exercises and simulations to ensure preparedness.
4. Strategic, Tactical, and Operational Intelligence
- Strategic Intelligence: Long-term trends and analyses to inform the educational institution’s security posture.
- Tactical Intelligence: Immediate threats and their technical indicators.
- Operational Intelligence: Day-to-day operations and necessary actions to mitigate threats.
5. Technology and Infrastructure
- Security Information and Event Management (SIEM): Deploy SIEM solutions for real-time analysis.
- Advanced Persistent Threat (APT) Protection: Implement solutions for APT detection and response.
6. Human Element
- Skilled Personnel: Assemble a team of skilled cybersecurity professionals with specialized knowledge in the educational sector.
- Continuous Training: Ensure ongoing training to keep pace with the evolving threat landscape.
Establishing a Threat Intelligence Team
Organizational Structure
- Lead Analyst: Heads the team and coordinates intelligence activities.
- Sector-Specific Analysts: Specialize in understanding the threats unique to different areas within the education sector.
Responsibilities
- Monitor Threat Landscape: Stay abreast of new and emerging threats.
- Intelligence Sharing: Collaborate with other educational institutions for broader threat intelligence.
Utilizing Threat Intelligence
Risk Assessment and Management
- Assessment Frameworks: Adopt frameworks like NIST for a systematic approach to risk assessment.
- Threat Modeling: Use threat modeling to anticipate potential attack vectors.
Threat Prioritization
- Severity Assessment: Determine the severity of threats based on potential impact and likelihood.
- Resource Allocation: Allocate resources effectively by prioritizing high-severity threats.
Cyber Threat Intelligence Tools
Selection and Deployment
- Comparative Analysis: Compare tools based on functionality, scalability, and ease of integration.
- Implementation Strategy: Develop a phased implementation strategy for new tools.
Best Practices
- Tool Integration: Ensure tools are well-integrated into the existing cybersecurity infrastructure.
- Automation: Leverage automation to process large volumes of data efficiently.
Case Studies and Data-Driven Insights
Review of Past Incidents
- Data Breach Analyses: Analyze past data breaches in the education sector to identify patterns and prevention strategies.
- Response Evaluation: Evaluate the effectiveness of incident responses.
Trend Analysis
- Threat Evolution: Track how threats have evolved over time.
- Preventive Measures: Determine the effectiveness of different preventive measures based on historical data.
Training and Education
In-House Training
- Curriculum Development: Develop training programs for cybersecurity staff.
- Simulated Attack Scenarios: Conduct training using simulated cyber attack scenarios.
Collaborative Learning
- Inter-Institutional Workshops: Organize workshops with other educational institutions.
- Industry Partnerships: Partner with cybersecurity companies for expert insights and training.
Challenges and Considerations
Budget Constraints
- Cost-Effective Solutions: Explore cost-effective TIC solutions without compromising on quality.
- Justification for Investment: Use data and case studies to justify TIC investment to stakeholders.
Privacy and Compliance
- Data Privacy Laws: Navigate data privacy laws while collecting and analyzing threat intelligence.
- Compliance Standards: Adhere to compliance standards like GDPR and FERPA.
Conclusion: The Road Ahead for TIC in Education
Developing a TIC is an ongoing process that requires dedication, resources, and a commitment to continuous improvement.
As cybersecurity threats evolve, so too must the tactics and strategies of those tasked with protecting the bastions of education.
By fostering a culture of security awareness and adopting a proactive stance towards threat intelligence, educational institutions can not only defend against cyber threats but can set a standard for cybersecurity excellence in the sector.







